Banner Grabbing Tools And Techniques Explained
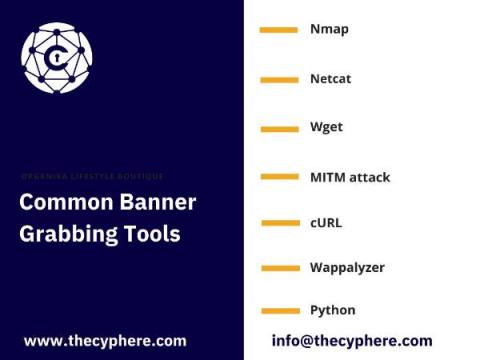
As we all know, whenever it comes to penetration testing, the first thing which comes to mind is reconnaissance. Banner grabbing is used in the initial phase of reconnaissance to get an idea about the target system or application.