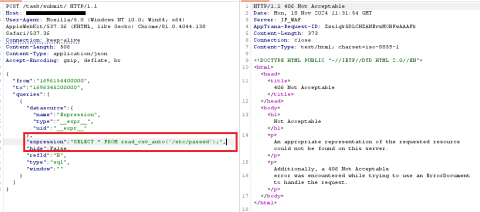
CVE-2024-9264 - Grafana's SQL Expressions Vulnerability
A critical vulnerability, CVE-2024-9264, has been discovered in Grafana, the open-source analytics and visualization platform widely used by organizations worldwide. According to Netlas.io, over 100,000 Grafana instances may be vulnerable globally, with nearly 19,000 in the U.S. alone. This vulnerability poses significant risks, enabling remote code execution (RCE), allowing attackers to execute arbitrary system commands and access sensitive files.