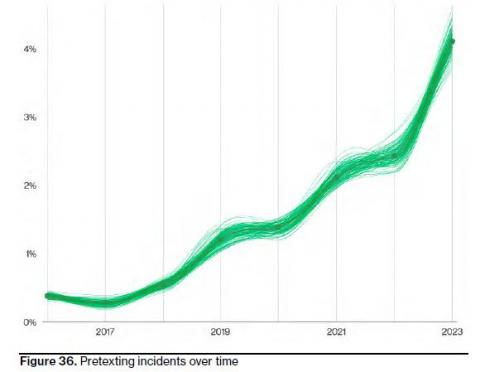
The face of 2023's cyber-threat landscape was an alarming surge in ransomware and phishing attacks
When KnowBe4 went public in April 2021, I got to know a select group of analysts that served as co-managers on our IPO. These professionals all know our industry very well and we spoke with them quarterly during our earnings conference call where we discussed the past 3 months and expectations for the future. One of these firms was Baird Equity Research and I am still on their mailing list, even though we went private this year as a Vista Equity Partners portfolio company.