Extending Your Fortinet FortiManager to Kubernetes
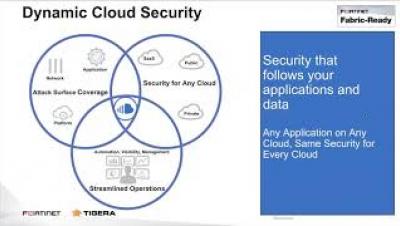
Tigera and Fortinet have joined forces to solve this operational challenge. With the combination of FortiManager and Calico Enterprise, you gain access control and full visibility into the container environment along with centralized management. In this webinar, you will learn how Calico Enterprise and FortiManager enable you to.