Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
opsdemon
Latest posts
Cybersecurity Dissonance: Perception vs Reality Panel Discussion
Arctic Wolf recently completed a cybersecurity survey and found that nearly every company has very high confidence in their security defenses. However, the survey also identified that IT/security professionals felt security was complex, and they found it difficult to focus on security because their role covered so many different areas.
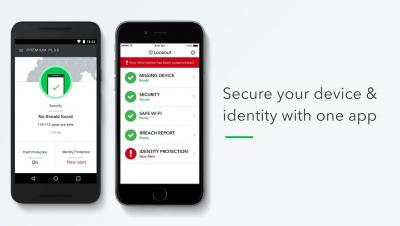
Lookout Identity Theft Protection and Breach Report
Lookout Identity Protection and Breach Report Secure your mobile device & identity with one app. Announcing new Identity Theft Protection for Lookout Personal.
MxLogic drawing to a close...But where next? What are the MxLogic alternatives?
MxLogic Slowly Draws To A Close Leaving Many In The Clutches Of Alternative Email Security Vendors. Change Can Be Tough For Admins And Users Alike…What Changes Has The Market Seen?
ZenGRC 2 minute overview
Watch how ZenGRC makes compliance easier for your compliance manager.
ZenGRC 4 minute overview
Watch how ZenGRC makes compliance easier for your compliance manager.
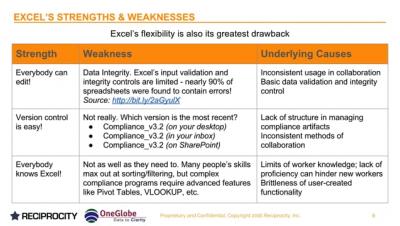
Competent Compliance: 3 Ways To Move Beyond Spreadsheets
While Microsoft Excel is flexible and powerful, it’s not designed to track compliance initiatives. Some companies can get away with using an Excel spreadsheet for simple compliance requirements. However as your organization matures the need for compliance software will quickly grow.
Cybersecurity Predictions: Mobile and PCs Will Converge
With adoption of Windows 10 in the enterprise, PC security architectures look like mobile security architectures.
Cybersecurity Predictions: The Network Perimeter Will Be Reborn
The future of cybersecurity includes a major change to enterprise network perimeters. They are going to be reshaped into something new — micro-perimeters. This is the act of cordoning-off entire sections of systems in order to avoid major compromise when only one segment of the architecture is weak.
Cybersecurity Predictions: Effectiveness is measured by risk reduction
In the past, security technology wasn’t as regularly tested in the “real world” as it is today. That is, breaches are happening and being publicized at a far higher rate than ever before. There are seemingly multiple breaches a week. This means the security technology behind those breaches may get 15 minutes of undesired fame and the CSO gets a meeting with her boss. Going forward, security vendors will need to answer the question, “Does this security technology work?” Security stakeholders within an enterprise will answer the question, “Does this security technology work for me?”
Cybersecurity Predictions: Your phone matters more than your password
The password may be one of the worst security elements we have. They are oftentimes easily guessed because we, as humans, are generally pretty bad at creating and remembering them. So, we use weak passwords across multiple accounts. We use simple passwords like “123456” or “password.” The industry is also yet to find something better. The phone, however, presents new and exciting ways for companies to protect their accounts, which means the phone is also become a critical part of the hacker “kill chain.”