Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
How to
DNS Traffic Analytics
In this video we will analyze the DNS traffic of a company to check whether the Internal Cache DNS Servers are resolving names correctly and accessing external Authoritative and Root DNS Servers in the most optimal way.
Monitoring Unix Machines with Devo
This video explains how to monitor Unix systems with the Devo Monitoring package, how Devo organizes these logs and how to activate the System Monitoring Application to evaluate the activity of Unix systems and configure alerts.
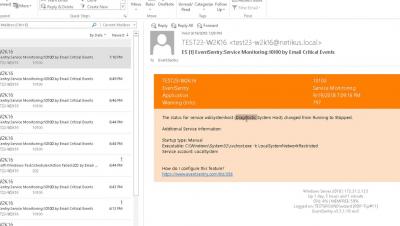
Process & Netstat Monitoring with EventSentry
Put netstat on steroids and reduce your attack surface by revealing all processes on your network that are listening for incoming TCP connections. EventSentry can also alert when a new process is listening for incoming connections, or when critical processes are not running.
Monitoring Windows Machines with Devo
How to monitor Windows systems with the Devo Windows Agent and how Devo organizes these logs and distributes them automatically into their appropriate tables.
Using Devo Panels
Devo offers a powerful feature called Panels, a powerful tool that creates diagrams and graphical displays of activities, alerts, and business processes.
Telefónica Transforms User Experience with Devo
Telefónica, the world's 7th largest telco provider, uses the Devo Data Operations Platform to measure and improve the user experience of their IPTV subscribers.
How to exclude alerts with EventSentry
Explains how to exclude email alerts in EventSentry using Outlook, the built-in event viewer, or manually.
Monitoring Access to Malicious Websites
How to monitor the access of potentially dangerous websites by employees.
Analyzing Website Status Codes
How to use Devo to analyze the status codes of an Apache web server.