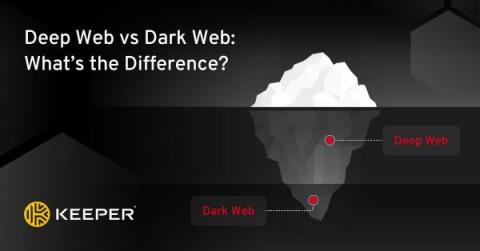
Demystifying the Dark Web and DarkNets, Part IV - Corporate Spies, Scammers, Spammers, Stalkers, and Cyber Criminals
September 7, 2023 Author: Anonymous Hacker, as told to Lindsey Watts Preface: Thus far in our series, we’ve looked at what DarkNet types exist in addition to the dark web, communication methodologies on DarkNets, social-ethical questions raised by anonymous, and unregulated and un-censored communication platforms. Your interest might be piqued at this point but if not hold onto your seat because it’s about to be.