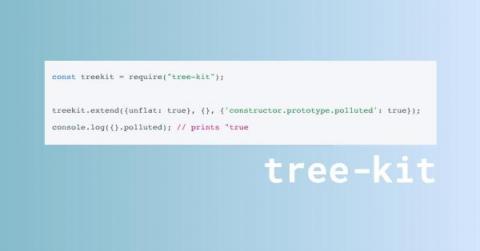
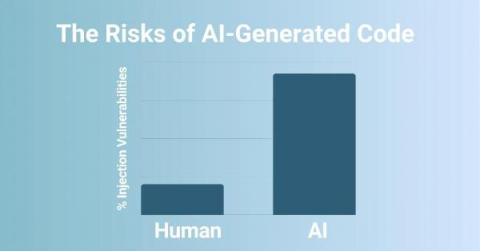
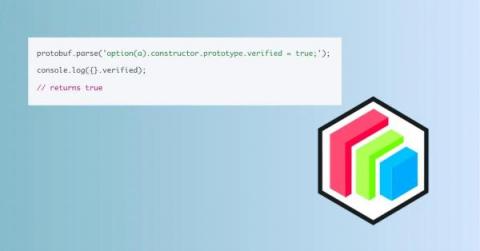
DevSecOps Talks - Mitigating the Risks of 3rd Party Code
In today's fast-paced software environment, third-party code has become irreplaceable. With 96% of codebases containing open-source dependencies, the image is clear: open-source is ubiquitous in the development landscape.