Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
JFrog
New .NET Malware "WhiteSnake" Targets Python Developers, Uses Tor for C&C Communication
The JFrog Security Research team recently discovered a new malware payload in the PyPI repository, written in C#. This is uncommon since PyPI is primarily a repository for Python packages, and its codebase consists mostly of Python code, or natively compiled libraries used by Python programs. This finding raised our concerns about the potential for cross-language malware attacks.
Software Supply Chain Security at RSA Conference 2023
The risk of supply chain attacks increases as more companies rely on third-party vendors and suppliers for critical services and products. Supply chain attacks have become increasingly prominent in recent years. In 2022, for instance, supply chain attacks surpassed the number of malware-based attacks by 40%.
Secrets Detection JFrog Security Workshop
Analyzing Impala Stealer - Payload of the first NuGet attack campaign
In this blog post, we’ll provide a detailed analysis of a malicious payload we’ve dubbed “Impala Stealer”, a custom crypto stealer which was used as the payload for the NuGet malicious packages campaign we’ve exposed in our previous post. The sophisticated campaign targeted.NET developers via NuGet malicious packages, and the JFrog Security team was able to detect and report it as part of our regular activity of exposing supply chain attacks.
See JFrog Advanced Security in Action
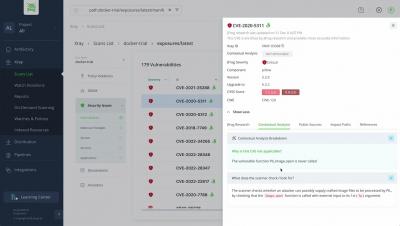
Zero Day Doesn't Mean Zero Hope
#zeroday #security #sca #devops #devsecops #devopssecurity #softwaresupplychain
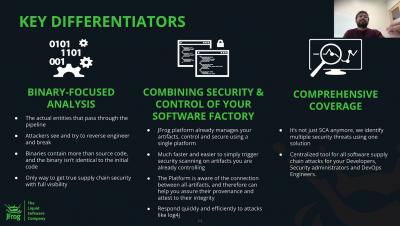
Save time fixing security vulnerabilities much earlier in your SDLC
Are you or your development team tired of using application security tools that generate countless results, making it difficult to identify which vulnerabilities pose actual risks? Do you struggle with inefficient or incorrect prioritization due to a lack of context? What adds insult to injury is that traditional CVSS scoring methods ignore critical details like software configurations and security mechanisms.
JFrog DevSecOps Triple Therapy
Learn more about bringing your Dev, Sec and Ops Teams together at https://jfrog.com/