Prioritization Changes the Game in DevSecOps
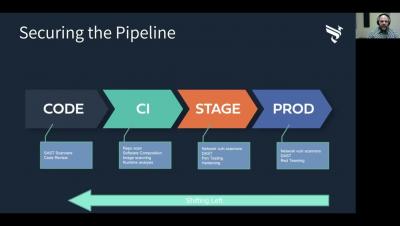
This is the third installment in a series about making DevSecOps work in your organization. We’ve looked at the first two pillars of the DevSecOps model—discovery and validation. In this post we examine the third—prioritization. Discovery enables security and development teams to identify software vulnerabilities, and validation allows them to determine which of these flaws present actual security risks and which do not.