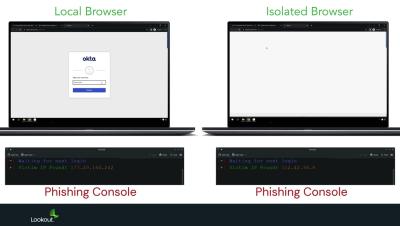
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Lookout
5 Trends That Are Changing the Landscape of Cybersecurity
Protect Users from Phishing and Malicious Content with SSE
Defending Against Modern Breaches: Lookout's Defense-in-Depth Solution
Your Data Has Moved to the Cloud - Can Your Security Strategy Keep Up?
Detecting Advanced Malware on Mobile Devices
Learn more: www.lookout.com/products/endpoint-security
Request a demo: www.lookout.com/contact/request-a-demo
Try Lookout Mobile Endpoint Security free for 90 days: www.lookout.com/contact/90-day-free-trial
How Lookout Mobile Endpoint Security Protects Against Evolving Threats
3 Things To Know About Securing Remote Work with VPN
It's been two decades since the introduction of virtual private networks (VPNs), and they are still the go-to solution for many organizations that need to connect remote users to company resources. But while VPN technology remained relatively static — grounded on the principle that your resources are primarily located on a corporate network — remote work requirements have changed dramatically.
Are Your Private Apps Secure? 3 Questions To Ask
Your data has left the premises. While virtual private networks (VPNs) used to be the go-to solution for extending access to private apps to remote users, they aren't a sufficient solution for securing a hybrid workforce. Because they place so much trust in users and devices, they end up granting overly permissive access to everything inside the perimeter, putting your data at risk.