Automate Non-Human Identity Security and Management with Torq and Astrix
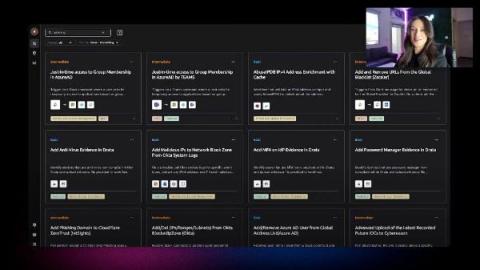
Organizations’ zero-trust policies and identity-centric programs ensure that user identities and login credentials are vigorously protected with IAM policies and security tools like MFA or IP restrictions. However, the situation is very different regarding non-human identities (NHI) like API keys, OAuth apps, service accounts, and secrets. Lack of visibility, monitoring, and governance of this permissive access is everywhere, and attackers have figured it out.