Rise of the Machines: The 2024 SOC Transformation
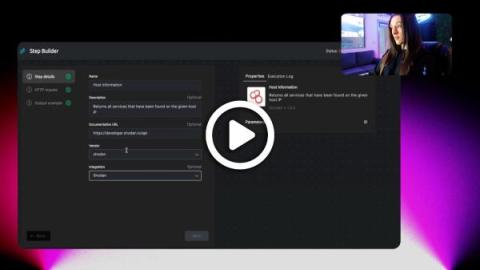
We’ve been taught to fear the rise of the machines. But what if machines taking over is a good thing? Leonid Belkind, our CTO and Co-Founder, sat down with Brittney Zec, our Senior Social Media & Content Manager to share insights on how AI-driven hyperautomation addresses the existential challenges SOC analysts face.