How Software Supply Chain Vulnerabilities Lead to Attacks
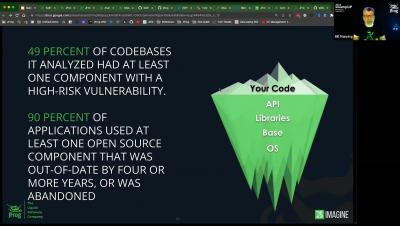
Software supply chain attacks are increasingly gaining attention. Why? Software developers today have grown increasingly reliant on vendors, suppliers, and partners, so the software supply chain has become a key factor in the ability to build new enterprise apps. This means more partners are touching sensitive data than ever before, and attackers have taken notice. More open-source components are being used and consequently, vulnerabilities are slipping in through the software supply chain.