Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Storage
Nextcloud Review: Is Self-Hosting Your Cloud Storage Worth It?
Top 5 Best Cybersecurity Training Mobile Apps
Gain access to the best cybersecurity training from anywhere, anytime, with these top 5 cybersecurity apps for iOS and Android 📱 Cybersecurity attacks are very common; learn which top 5 cybersecurity tools and apps can help you to prevent them 🛡️ Learn more at https://internxt.com/cyber-awareness
5 Websites with the Best Cybersecurity Courses
Learn the 5 best cybersecurity websites, including the best cybersecurity courses, best cybersecurity training, top cybersecurity certifications, and more! 💭 We will help you start your cyber journey today! 🚀 Learn more at https://internxt.com/cyber-awareness
Top 5 Cybersecurity Tools for Beginners & Pros
Want to know more about how the cybersecurity world works? Wondering where to start with cybersecurity? 🌐 Learn the top 5 cybersecurity tools and platforms professionals and hobbyists use for ethical hacking, debugging, and more! 💻 Learn more at https://internxt.com/cyber-awareness
The 5 Best Cybersecurity Tips for Online Safety
October is Cybersecurity Awareness Month! 🛡️ Let’s start by adding some cyber security daily tasks into your cyber hygiene routine to defend yourself against the top cybersecurity attacks with the best cybersecurity tips 💪 Learn more at: https://internxt.com/cyber-awareness
Managing Storage Access: Secure Cloud-native Development Series
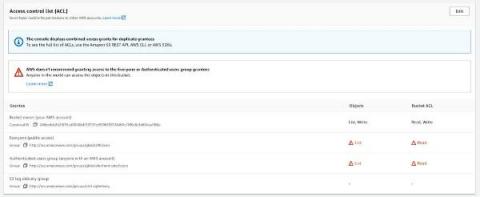
Build secure cloud-native applications by avoiding the top five security pitfalls we lay out in our Secure Cloud-native Development Series. This blog is the third part of the series, and it will teach you how to secure cloud storage and handle access controls on S3 buckets. Each cloud provider has managed storage services that your organization is already probably utilizing.
Upgrade Your Cloud Storage Experience With This Alternative to Filen
Don't Choose a Cloud Storage Service Without Asking These 10 Critical Cybersecurity Questions
More InterPlanetary File System Services Use Also Means Phishing Abuse by Cybercriminals
The InterPlanetary File System (IPFS), a distributed file-sharing system that represents an alternative to the more familiar location-based hypermedia server protocols (like HTTPS), is seeing more use in file-storage, web-hosting, and cloud services. As might be expected, more use is accompanied by more abuse via phishing attacks.