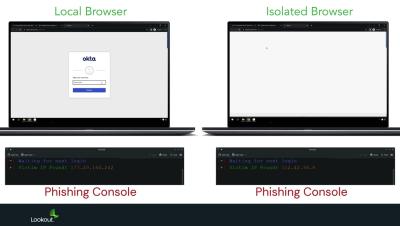
Today, cloud breaches happen in minutes. Not months. Attackers, with just the right login, can instantly access your data. To halt a breach, identifying and blocking data theft is essential. Prevention, however, begins with securing mobile devices. which are often unprotected, are highly susceptible to social engineering. Lookout adds depth to your defense with security that works at every turn. This includes blocking text messages that steal credentials and preventing compromised accounts from accessing your data. With Lookout, rest assured that your cloud data flows freely, and securely.