CrowdStrike Cloud Infrastructure Entitlement Management (CIEM)
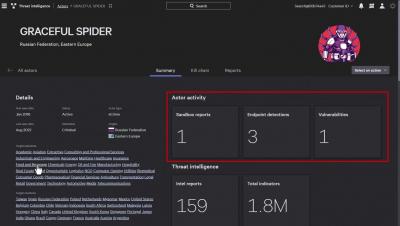
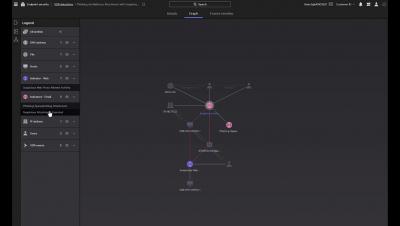
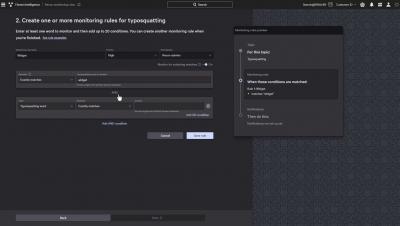
Identity theft and overly permissive accounts are major challenges faced by organizations in public and hybrid cloud environments. Learn how CrowdStrike Cloud Infrastructure Entitlement Management (CIEM) can increase the security of your cloud infrastructure while simplifying management across clouds.