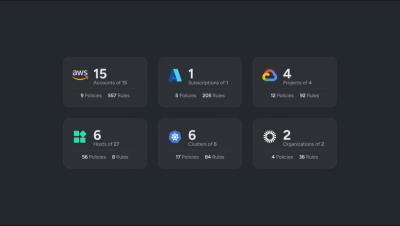
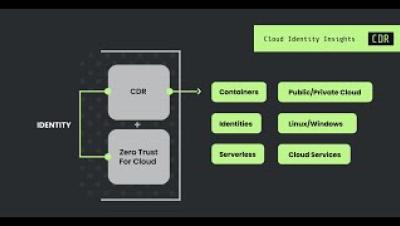
Sysdig's Cloud Workload Protection Platform (CWPP)
The cloud transformed innovation. But, a lack of visibility into complex workloads, thousands of vulnerabilities add a lot of noise. With Sysdig, you can streamline container and workload security and get back to innovating. Secure every second with Sysdig!