Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
What is IOC in Cyber Security?
Indicator of compromise or IOC is a forensic term that refers to the evidence on a device that points out to a security breach. In this article, we discussed how IOC can be useful for your cyber security team.
What is Return on Security Investment? How to Measure the Return on Investment (ROI)?
It is crucial to invest in cyber security due to state of cybersecurity today. Before making any decisions concerning the security posture of your business, you must consider the Return on Security Investment. In this article, we took a closer look at what ROSI is and how it is calculated.
Cyber Risk Management Framework
Data is regarded as the most valuable asset in today’s business world. The examples of critical data include e-commerce data, e-banking data, and Personally Identifiable Information (PII). Therefore, data security is, and data breaches have become an international concern for individuals as well as organizations. The role of the Cybersecurity Risk Management Framework (RMF) in data security is indispensable.
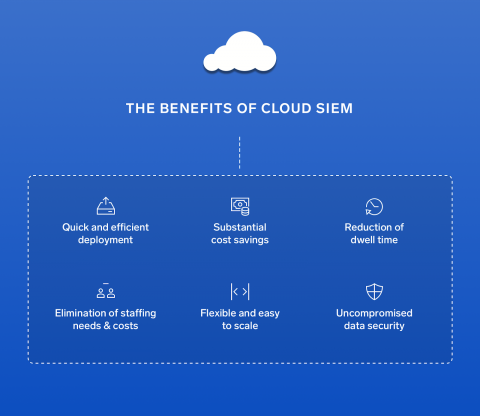
The Next-gen Cloud SIEM Must Empower Analysts
Digital transformation is creating rapidly growing volumes of data, leading to new vulnerabilities and attack vectors. At the same time, adversaries are growing increasingly more sophisticated – consider the recent Capital One breach, or the Equifax breach. This combination of factors means SOCs are struggling to fulfill their critical mission of identifying and eliminating threats.
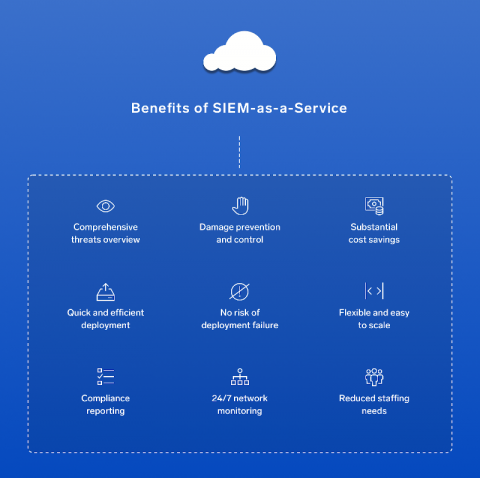
What Is the Difference Between SIEM and SOAR?
Nowadays, a lot of attention is being paid on the SOAR vs. SIEM debate. To get the most benefit from your security data, it is vital to understand the difference between these essential cybersecurity tools. Although SOAR and SIEM have several components in common, we cannot use these tools interchangeably as they are different in nature.
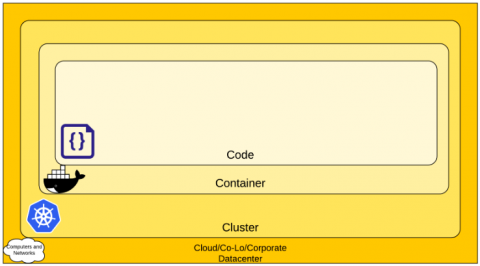
How to SIEMplify through Cloud SIEM
10 Best SIEM Use Cases (Part 2)
SIEM security that is equipped with Artificial Intelligence (AI) and user behavior analytics can deal with internal threats. AI capabilities in SIEM help security professionals to automate tasks that are otherwise manual and repetitive. Doing so can also help to swiftly detect threats and suspicious activities in network traffic and event logs.
To SIEM or not to SIEM?
What is a SIEM Use Case?
In regard to rising trends and forms of attacks, a growing number of organizations opt for SIEM solutions so that they can provide a proactive measure for threat management and also acquire a detailed and centralized view of the overall security measures of their organization. Since SIEM is the foundation of a security infrastructure, there are large varieties of SIEM use cases.