What to Expect with Bitsight's 2024 Ratings Algorithm Update
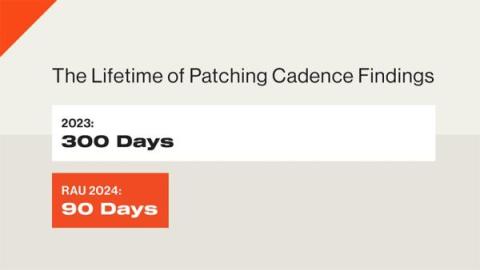
As communicated in January, Bitsight will conduct a ratings algorithm update (RAU) on July 10, 2024, as part of our ongoing efforts to optimize our methodology to provide the best external indicator of the performance of cybersecurity controls. Today, we’re excited to announce that our 2024 RAU is available to preview in the Bitsight applications.