Unveiling CPS 234 Challenges: Insights from APRA's Cyber Security Stocktake
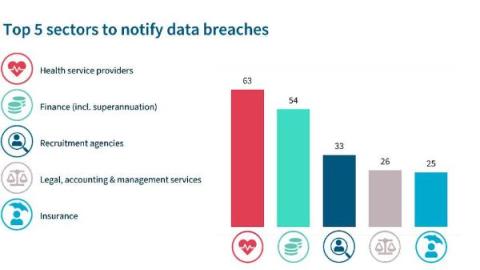
Australia has seen several high profile cyber incidents in 2023 and has seen significant loss of customer data (Canva’s 139 million customers, Latitude’s 7.9 million customers HWL Ebsworth’s 65 government agencies, 2.5 million documents). According to the OAIC Notifiable Data Breaches Report: January to June 2023, the top 3 sectors in that period to report data breaches are Health Service Providers (65 notifications), Finance incl.