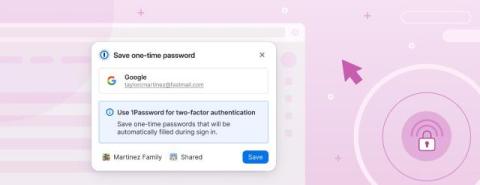
1Password product enhancements [Winter edition]: Mobile improvements, better item creation, and even more security features
Making 1Password intuitive and easy to use is a top priority. That’s why we spent all of 2024 introducing many improvements and new features to create the best customer experience possible.