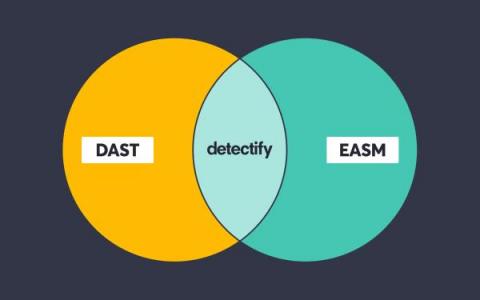
How Detectify embraces the best of both DAST and ASM
Below, we’ll take a look at how both DAST as a methodology and DAST as a tool relate to what we do at Detectify. More specifically, we’ll explain how Detectify’s solution applies DAST methodology to the full breadth of an attack surface, automating the heck out of application security testing. With these methods, we cover millions of domains before you’ve even had breakfast.