Why Security Strategies Should Matter to the CIO
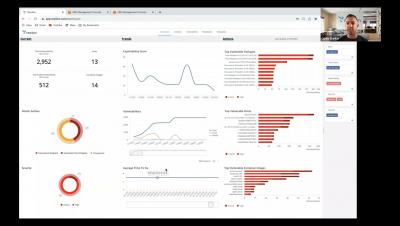
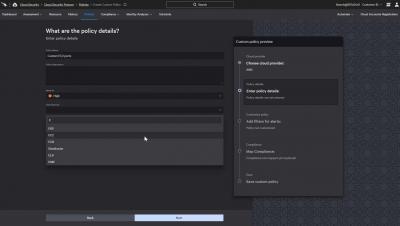
In the face of this constant disruption, CIOs are supporting the addition, amendment, or strengthening of logistics workflows, supply chains, commercial and service delivery models, partnerships, and geographic footprints. In all of these programmes, CIOs often see cybersecurity as a hurdle—one more challenge to navigate in the path to a successful business outcome.