Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2024
Ransomware Payments On The Decline As Cyber Attackers Focus on The Smallest, And Largest, Organizations
Open Redirects Used to Disguise Phishing Links
The Percentage of Organizations Globally Struck by Ransomware Hits an All-Time High
Identify Weak User Passwords With KnowBe4's Enhanced Weak Password Test
Malvertising Targets Chinese-Speaking Users
Forget Deepfake Audio and Video. Now There's AI-Based Handwriting!
Scammers Use Airdrops to Lure Users With Phony NFTs
Social Engineering Attacks Rising in the Trucking Industry
New Evasive Phishing Technique "Legacy URL Reputation Evasion" (LURE)
HP Enterprise Reveals It was hacked by the same Russians that broke into Microsoft
The Number of Ransomware Attack Victims Surge in 2023 to over 4000
North Korean Threat Actor Targeting Cybersecurity Researchers With Spear Phishing Attacks
Use of Generative AI Apps Jumps 400% in 2023, Signaling the Potential for More AI-Themed Attacks
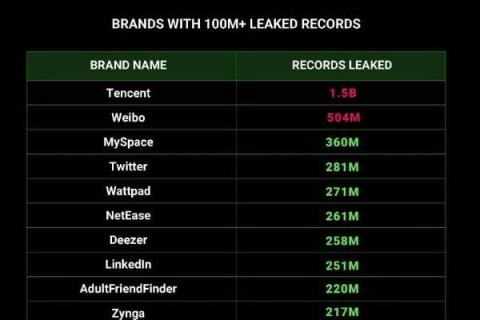
Unprecedented Cybersecurity Alert: 26 Billion Records Exposed in Mega Data Breach
Russian State-Sponsored Threat Actor Targets High Profile Individuals in Phishing Campaign
AI Does Not Scare Me, But It Will Make The Problem Of Social Engineering Much Worse
Facebook Phishing Scams Target Concerned Friends and Family
KB4-CON 2023 Demo Presentation
Check out the blog post: https://blog.knowbe4.com/ai-does-not-scare-me
And make sure to register for KB4-CON 2024: https://www.knowbe4.com/kb4-con
Russian Hackers Win Big: Microsoft's Senior Exec Team Emails Breached
More Than Half of Data Breaches in the U.K.'s Legal Sector are Due to Insider Error
A new analysis of data breaches in the United Kingdom's legal sector shows that organizations need to be looking inward more and look for ways to elevate the security awareness of employees. There’s so much focus on external cybercriminal activity, we often forget about the actions of internal employees that often facilitate a data breach.
Scammers Target Owners of Missing Pets
Some particularly cold-hearted scammers are targeting users of lost pet forums with phony ransom demands, the BBC reports. “A BBC North West investigation found scammers have targeted scores of dog and cat lovers with threatening calls,” the BBC says. “They prey on owners by claiming to have their lost pets before demanding cash.
Ninety-Four Percent of Organizations Sustained Phishing Attacks Last Year
A survey by Egress has found that 94% of organizations were hit by phishing attacks in 2023, Infosecurity Magazine reports. Additionally, 91% of firms experienced data loss and exfiltration. The three most common causes of data loss were reckless behavior, human error and malicious exfiltration.
'Swatting' Becomes the Latest Extortion Tactic in Ransomware Attacks
Rather than stick to traditional ransomware extortion methods that revolve around the attack itself, a new form of extortion known as Swatting puts the focus on the victim organization’s customers. A somewhat unexpected mode of extortion appears to be popping up in attacks targeting medical institutions. According to Dark Reading, cybercriminals are making repeat prank calls to police about individuals that are patients impacted by a data breach of a medical facility they are a customer of.
Malicious APKs Drain Bank Accounts
A phishing campaign is targeting Chinese users in an attempt to distribute malicious apps, according to researchers at Palo Alto Networks’s Unit 42. "The threat actor masquerades as a law enforcement official and says the target's phone number or bank account is suspected of being involved in financial fraud,” the researchers write. “They then guide the person to download an app that will allow the attacker to investigate their bank transactions.
Cryptocurrency Drainer Distributed Through Phishing
Mandiant has published a report on “CLINKSINK,” a cryptocurrency Drainer-as-a-Service (DaaS) that’s targeting users of the Solana currency. Mandiant’s own X (formerly Twitter) account was hacked earlier this month and used to distribute a link to the drainer. Threat actors using CLINKSINK have stolen at least $900,000 worth of cryptocurrency in recent weeks.
LinkedIn is Being Used for *Dating* - It's a Recipe for Disaster
A new article explains how business professionals are beginning to be not-so-professional and seeking to make personal connections. It’s only a matter of time before cybercriminals jump in. I came across a recent Business Insider article entitled, “The hottest new dating site: LinkedIn.” The title made me laugh… and then when I put my cybersecurity hat back on, the laughing stopped.
Three-Quarters of Organizations Have Experienced Phishing Attack in the Last 12 Months
Regardless of whether your environment remains on-premise, resides in the cloud, or is a hybrid configuration, new data makes it clear that your biggest risk is phishing attacks. According to Netwrix’s 2023 Hybrid Security Trends Report, released late last month, 73% of organizations have some form of hybrid environment, with slightly less than half of all workloads (44%) residing in the cloud.
Women CyberSecurity Society Targeted by Smishing Campaign
The Canada-based Women CyberSecurity Society (WCS2) has warned that its leadership, members, and volunteers are being targeted by an SMS phishing (smishing) campaign, IT World Canada reports. “A volunteer recently reported receiving a text message claiming to be from founder Lisa Kearney citing an urgent need for help,” WCS2 says.
Analysis of Phishing Emails Shows High Likelihood They Were Written By AI
It’s no longer theoretical; phishing attacks and email scams are leveraging AI-generated content based on testing with anti-AI content solutions. I’ve been telling you since the advent of ChatGPT’s public availability that we’d see AI’s misuse to craft compelling and business-level email content.
Outstanding ROI of Security Awareness Training
KnowBe4 Named a Leader in the Winter 2024 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Winter 2024 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR) for the PhishER platform for the eleventh consecutive quarter! The latest G2 Grid Report compares Security Orchestration, Automation, and Response (SOAR) Software vendors based on user reviews, customer satisfaction, popularity and market presence.
FTC Issues Warning About the Dangers of QR Code-Based Scams
The latest consumer alert posted by the federal trade commission (FTC) signals that the upticks in QR code-based scams are being seen by cybersecurity vendors are indeed a valid growing problem. You won’t need to go very far before you find a QR code. Restaurants commonly use QR codes to point you to a menu, parking lots use them to point you to a website to pay for parking, and according to the FTC, scammers use them to engage you in scams.
Microsoft Takes the Lead in Q4 2023 for Alarming Phishing Attempts
Microsoft was the most impersonated brand last quarter, accounting for a third (33%) of all brand phishing attempts in October, November, and December 2023, according to Check Point’s Brand Phishing Report for Q4 2023. Check Point notes, “The technology sector stood out as the most targeted industry overall, with Amazon securing second place with 9% and Google in third at 8%.
Beware of "Get to Know Me" Surveys
Trained security awareness professionals are aware that whatever someone says about themselves and personal experiences can be used against them in a social engineering scam. It is always good to share that message, at least once a year with co-workers, family members, and friends. I was reminded of this latest news story discussing a recent Instagram and TikTok trend. Basically, users are sent (or send) a “survey” that asks the receiver to describe themselves.
KnowBe4 Named a Leader in the Winter 2024 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares security awareness training (SAT) vendors based on user reviews, customer satisfaction, popularity and market presence. Based on 1,455 G2 customer reviews, KnowBe4’s KMSAT is the top ranked SAT platform with 98% of users rating 4 or 5 stars. The KMSAT platform received the highest G2 score among products in the SAT category with a score of 93 out of 100.
Red Flags for Phishing: Verizon Outlines Common Scams to Watch Out For
Verizon has published an article outlining various forms of social engineering attacks, including SMS/text messaging phishing (smishing), voice phishing (vishing), and spear phishing (targeted attacks, often via email). Verizon warns users to be on the lookout for the following red flags: Verizon concludes, “Remember, phishing is common and perpetrators are hoping to catch you with your guard down. But most companies will never proactively reach out to you.
Cybercriminals Celebrate the Holidays with Dark Web Data Dumps, Dubbed "Leaksmas"
Millions of data records and GBs of data from organizations around the globe were made freely available to cybercriminals to coincide with dates around Christmas of 2023. The pressure presented by cybercriminals threatening to publish data on the web is very compelling. After all, what company wants to be responsible for millions of everyday people potentially becoming victims of scams and cyber attacks? That’s right, not a single one.
FBI Releases Blackcat Ransomware Decryption Tool to Victims, Disrupting Attacks
For the first time ever, the U.S. Justice Department announced the existence of an FBI-developed decryption tool that has been used to save hundreds of victim organizations attacked by one of the most prolific ransomware variants in the world. In an announcement made last month, the Justice Department made the world aware of the existence of a decryption tool to be used by those organizations hit by Blackcat – also known as ALPHV or Noberus.
Phishing Reigns as the Most Likely and Most Feared Cyber Attack
With over half of organizations being the victim of password-based attacks in the last year, new data sheds light on the risk of phishing attacks and the use of password-based credentials. If you don’t think credentials are a key element in cyber attacks, I refer you back to an article of mine from the middle of last year where 15 billion (with a ‘b’) credentials are on sale on the dark web.
Out of the Shadows: Resecurity Exposes 'GXC Team' - Architects of Cybercrime in Online Banking and Social Engineering
Resecurity is tracking a cybercriminal gang called “GXC Team” that develops and sells tools to facilitate online banking theft and social engineering attacks. In November, the gang began selling a tool that uses artificial intelligence to craft fraudulent invoices for use in business email compromise (BEC) attacks. The invoices can hijack business transactions by replacing banking information contained in legitimate invoices.
Beware of Fraudulent Charge Messages
Be careful of emails, SMS messages, or calls claiming to be from your bank about your card being used fraudulently. If this ever happens, call the phone number on the back of your card. This is a very common sort of social engineering fraud. Do not get scammed like TV host Andy Cohen did.
Black Basta Ransomware Decryptor Released to Help Some Victims
A flaw found by security researchers in the encryption software allows victim organizations to use “Black Basta Buster” to recover some of their data – but there’s a catch. We’ve all heard – for as long as ransomware attacks have been happening, you either need to pay the ransom or recover from backups. But a third option has now sprouted up on GitHub.
New Research: Phishing Attacks Stole $295 Million In Crypto In 2023
Researchers at Scam Sniffers have found that phishing attacks stole nearly $295 million worth of cryptocurrency from 324,000 victims in 2023, CryptoSlate reports. The cryptocurrency is stolen by malware delivered via phishing sites. “Wallet Drainers, a type of malware related to cryptocurrency, has achieved significant success over the past year,” the researchers write.
Lockbit 3.0 Ransomware Disrupts Emergency Care at Multiple German Hospitals
Hitting three hospitals within a Germany-based hospital network, the extent of the damage in this confirmed ransomware attack remains undetermined but has stopped parts of operations. It appears that affiliates of ransomware gangs have forgotten the golden rule – you don’t hit hospitals. It’s one thing to disrupt operations at a regular brick and mortar business. But hitting a business where someone’s life could be literally placed in jeopardy because a system is unavailable?
A Dream Team Security Awareness Training Program?
Every person and organization is different and requires slightly different methods and ways of learning. But every person and organization can benefit by more frequent security awareness training (SAT). Most organizations do not do enough. Training and testing once a year certainly is not that helpful. How often should you do SAT to get the biggest decrease in cybersecurity risk? At least once a month, if not more. But a sophisticated SAT program includes a combination of methods and tools.