Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
November 2022
Build Secure Java Applications with Fuzz Testing
Today, I want to show you a way how to increase the integrity and functionality of your Java applications, with fuzz testing. This awesome testing approach has done me great service for building more secure Java applications, and it's basically as simple as unit testing. In this article, I will share how you can apply fuzz testing to your own code. And the best part: all code examples and tools I will use are 100% open-source.
Fuzzing Java Applications With CI Fuzz | Gradle
Fuzzing Java Applications With CI Fuzz | Maven
Mock Testing Embedded Systems With Fuzz Data
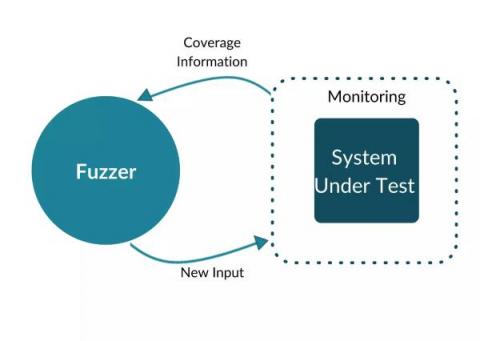
Mock testing, also called mocking, is an integral part of the embedded software development process as it allows you to test your code without relying on actual hardware. This can be extremely helpful when trying to debug your code or test new features. During fuzzing testing, applications are tested using unexpected or invalid inputs. Modern fuzzers generate these inputs based on feedback about the SUT’s interaction with previous test inputs.
The Benefits of Negative Testing in Software Testing
In software testing, negative testing refers to the practice of feeding a system with unexpected or invalid inputs. Given an input field that accepts numeric values from 0-100, positive tests would assess if the application does what it's supposed to do, given input values such as "1", "2" or "99".
Bridging the Gaps of Grey-box Fuzzing | FuzzCon Europe - Automotive Edition 2022
How To Improve Automotive Security | FuzzCon Europe - Automotive Edition 2022
Fuzzing beyond Cybersecurity | FuzzCon Europe - Automotive Edition 2022
Historical Vulnerabilities in the Automotive Space | FuzzCon Europe - Automotive Edition 2022
FuzzCon Europe - Automotive Edition 2022
Embedded Testing Tools: A Comprehensive Guide
Due to increasing connectivity and dependencies, modern embedded applications in many industries including automotive, aviation, and even automated cow brushes (no joke) are constantly growing more complex. This complexity comes with implications for embedded testing tools and requires plenty of manual effort, depending on the toolchain. From an operational perspective, many embedded industries are tightly staffed and work in long cycles with strict deadlines.
How Can Fuzzing Help Find Bugs in Hardware?
The growing complexity of embedded systems coupled with the advent of increasingly sophisticated security attacks highlights a dire need for advanced automated vulnerability analysis tools. Fuzzing is an effective proven technique to find security-critical issues in systems, often without needing to fully understand the internals of the system under test.
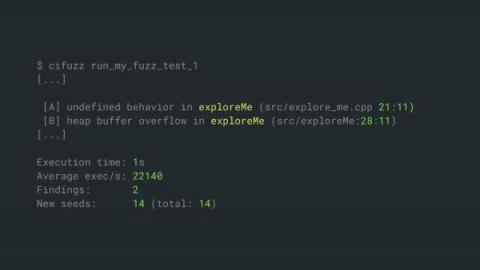
Secure Coding in C and C++ Using Fuzz Testing
Today, I would like to show you to a simplified fuzz testing approach that enables secure coding of C and C++ applications. If you read this article to the end, you will learn about an automated security testing approach for C/C++ that can protect your applications against all sorts of memory corruptions and other common C/C++ vulnerabilities.