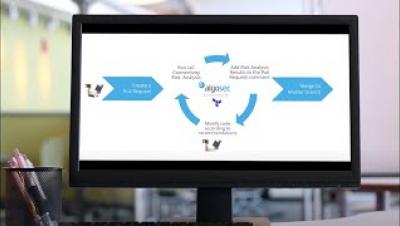
Continuous compliance monitoring best practices
As organizations respond to an ever-evolving set of security threats, network teams are scrambling to find new ways to keep up with numerous standards and regulations to dodge their next compliance audit violation. Can this nightmare be avoided? Yes, and it’s not as complex as one might think if you take a “compliance first” approach.