Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
March 2022
Cybersecurity Risk Management: Introduction to Security Analytics
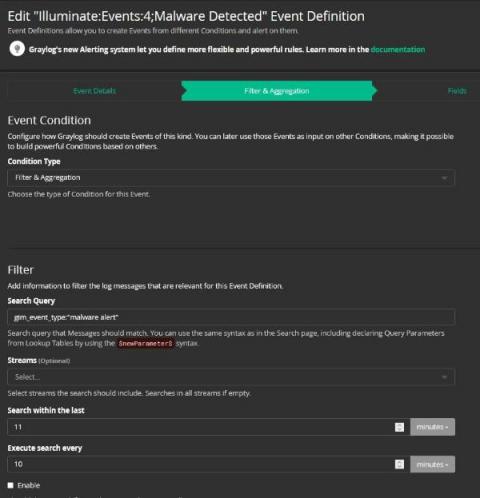
Centralized Log Management and NIST Cybersecurity Framework
It was just another day in paradise. Well, it was as close to paradise as working in IT can be. Then, your boss read about another data breach and started asking questions about how well you’re managing security. Unfortunately, while you know you’re doing the day-to-day work, your documentation has fallen by the wayside. As much as people are loathed to admit it, this is where compliance can help.
The Importance of Log Management and Cybersecurity
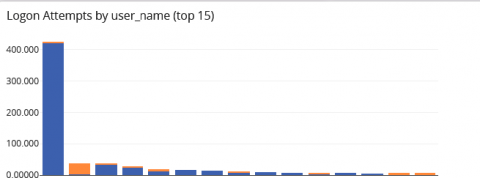
Struggling with the evolving cybersecurity threat landscape often means feeling one step behind cybercriminals. Interconnected cloud ecosystems expand your digital footprint, increasing the attack surface. More users, data, and devices connected to your networks mean more monitoring for cyber attacks. Detecting suspicious activity before or during the forensic investigation is how centralized log management supports cybersecurity.
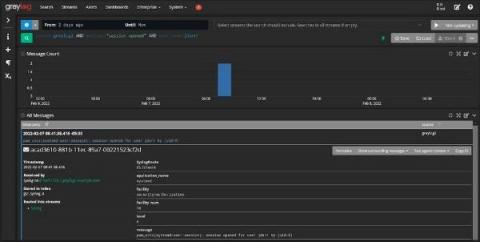
Using Centralized Log Management for ISO 27000 and ISO 27001
As you’re settling in with your Monday morning coffee, your email pings. The subject line reads, “Documentation Request.” With the internal sigh that only happens on a Monday morning when compliance is about to change your entire to-do list, you remember it’s that time of the year again. You need to pull together the documentation for your external auditor as part of your annual ISO 27000 and ISO 27001 audit.
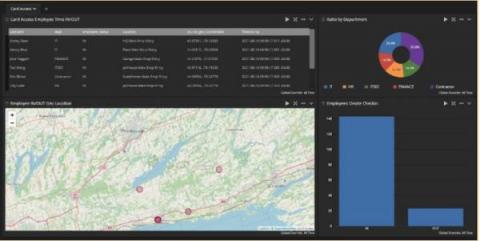
Using Log Management for Compliance
It’s that time of the year again. The annual and dreaded IT and security audit is ramping up. You just received the documentation list and need to pull everything together. You have too much real work to do, but you need to prove your compliance posture to this outsider. Using log management for compliance monitoring and documentation can make audits less stressful and time-consuming.