Friday Flows episode 36: Using Tines Workbench for asset and vulnerability management
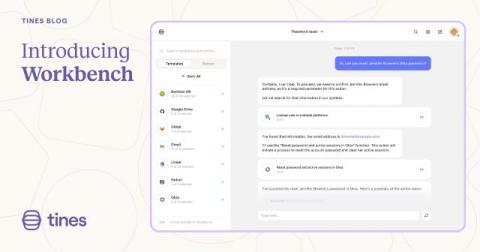
Michael Tolan from Tines Labs returns with Cameron for another episode on Tines Workbench. In case you missed it, Workbench is a Tines-powered AI chat interface where you can take action and access proprietary data in real-time, privately and securely. This episode leverages Workbench to make a tedious process extremely simple to handle. For any teams spending a lot of time on asset and vulnerability management, this is a must-watch!