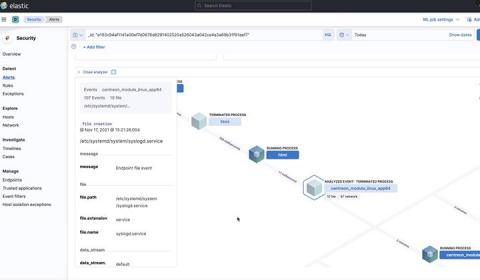
Detect Credential Access with Elastic Security
Within our Elastic Security research group, a strong area of focus is implementing detection mechanisms for capabilities we understand adversaries are currently exploiting within environments. We’ll often wait to see the impact that bringing these capabilities to market will have from a detection standpoint. This allows our researchers to explore different detection strategies through these additions, providing deep insight into how effective the Elastic Security platform can be.