Quick Start Guide: Integrate Veracode in Your DevOps Pipeline
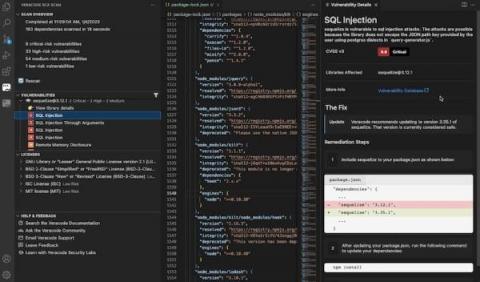
For today’s DevSecOps teams, the demands continue to intensify. Application portfolios and codebases continue to grow, while cyberattacks remain an ever-present danger. More than ever, it’s vital to ensure security gaps are identified and addressed with maximum speed and efficiency. In order to do this, you need to establish a continuous feedback loop on security threats, so you can realize optimized, sustained results – which is exactly how Veracode helps.