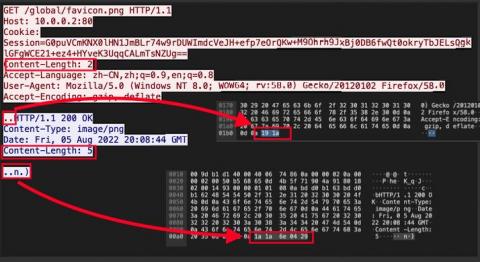
Detecting the Manjusaka C2 framework
Security practitioners may know about common command-and-control (C2) frameworks, such as Cobalt Strike and Sliver, but fewer have likely heard of the so-called Chinese sibling framework “Manjusaka” (described by Talos in an excellent writeup). Like other C2 frameworks, we studied the Manjusaka implant/server network communications in our lab environment, and here we document some of the detection methods available. We have also open-sourced the content we describe.