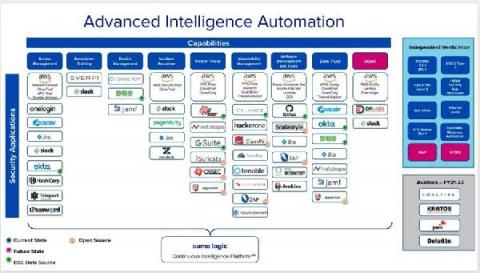
Supply Chain Security, Compliance, and Privacy For Cloud-Native Ecosystems
Think of the software supply chain as every software element in your organization—from software development of internal systems to open source or third-party enterprise software to vendors, partners, and even past suppliers who still hold access to company data or IT systems. Attacks on this software supply chain can damage individual departments, organizations, or entire industries by targeting and attacking insecure elements of your software fabric.