Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2021
Securing Access to Production MySQL Databases.
MySQL brands itself as the world’s most popular open source database. As popular as MySQL database is among developers and SQL enthusiasts, it is equally popular amongst hackers. Misconfigured server access, overprivileged roles, and weak authentication schemes are the most common security issues in MySQL database. While access control features provided by MySQL are adequate enough at the SQL level, it is error-prone to manage access at the operational level.
Securing DevOps : Security in the Cloud
Tagging Teleport Resources with Labels
Teleport has been named a Cool Vendor in Gartner's Identity-First Security report
Today we are happy to announce that Teleport has been included as a Cool Vendor in Gartner Cool Vendors in Identity-First Security report. “We believe Teleport’s inclusion in the Identity-First Security Report by Gartner is confirmation that Teleport solves a huge problem of accessing cloud-native resources that traditional PAM tools did not,” said Ev Kontsevoy, co-founder and CEO of Teleport.
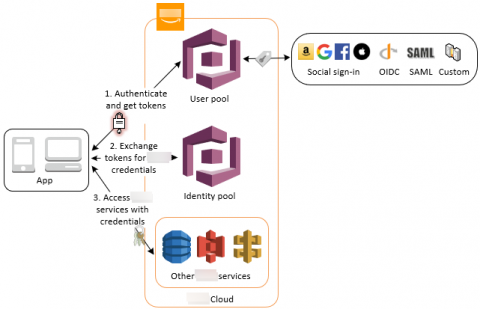
How does AWS IAM role, STS and Identity Pool work with each other.
We talked about IAM in the past 3 posts, identities in IAM, manage users privilege as an IT person and control privilege boundaries. We also talked about how applications use AWS Cognito Identity Pool to get AWS temporary credentials to access AWS resources in early posts of “What I wish I could have learned before starting using AWS Cognito” and “Authentication and authorization with AWS Amplify under the hood”.
Sharing SSH Sessions with Teleport
AWS IAM in a layman's terms
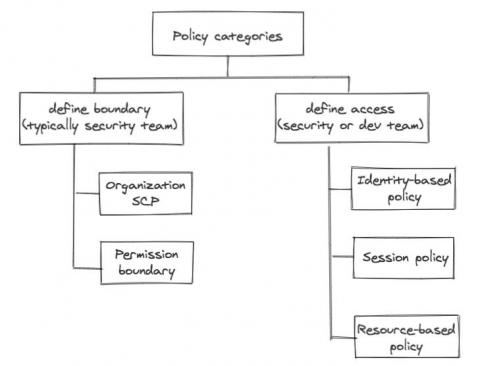
We alluded in one of our previous posts that the development team will own a lot of responsibility defining application related resource access control, simply because the dev team owns the infrastructure as code (IaC) responsibility themselves. No matter how security-savvy and security-educated a development team is, the central security team still needs some control, some kind of “trust but verify”.