Penetration Testing as a Service (PTaaS): What is it and How Can it Benefit Your Organization?
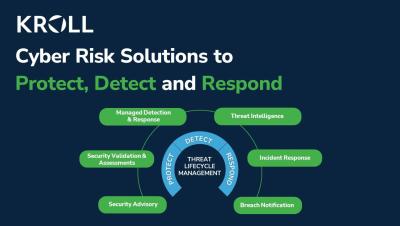
Learn about careers with us and search open job opportunities here. Penetration testing as a service (PTaaS) plays a vital role in enabling organizations to mitigate enhance their cyber posture. As a hybrid security solution, it combines automation and human assessments in order to test for vulnerabilities that could be missed by legacy scanning tools.