Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2022
Falcon Fusion Accelerates Orchestrated and Automated Response Time
In the recent MITRE Engenuity ATT&CK Enterprise Evaluation — which emulated today’s two most sophisticated Russian-based adversaries, WIZARD SPIDER and VOODOO BEAR (Sandworm Team) — CrowdStrike Falcon achieved 100% automated prevention across all of the evaluation steps.
CrowdStrike Delivers Adversary-Focused, Platform Approach to CNAPP and Cloud Security
Cloud-based services have revolutionized business processes and emerged as the backbone of the modern enterprise. According to analyst firm Gartner®, “more than 85% of organizations will embrace a cloud-first principle by 2025 and will not be able to fully execute on their digital strategies without the use of cloud-native architectures and technologies.”
Navigating the Five Stages of Grief During a Breach
Every security professional dreads “The Phone Call.” The one at 2 a.m. where the tired voice of a security analyst on the other end of the line shares information that is soon drowned out by your heart thumping in your ears. Your mind races. There are so many things to do, so many people to contact. You jump out of bed. For a moment, you stare into the mirror longing for yesterday — when your network hadn’t been breached.
LemonDuck Targets Docker for Cryptomining Operations
The recent cryptocurrency boom has driven crypto prices through the roof in the last couple of years. As a result, cryptomining activities have increased significantly as attackers are looking to get immediate monetary compensation. According to the Google Threat Horizon report published Nov. 29, 2021, 86% of compromised Google Cloud instances were used to perform cryptocurrency mining.
CrowdStrike Falcon Spotlight Fuses Endpoint Data with CISA's Known Exploited Vulnerabilities Catalog
The U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Agency (CISA) has been quite busy this year. It recently issued a “Shields Up” advisory, highlighting that “Russia’s invasion of Ukraine could impact organizations both within and beyond the region,” including the threat of malicious activity against U.S. interests and companies.
Security Doesn't Stop at the First Alert: Falcon X Threat Intelligence Offers New Context in MITRE ATT&CK Evaluation
CrowdStrike recently demonstrated the power of the Falcon platform and its integrated approach to providing robust protection by exposing all attack tactics used as part of the MITRE Engenuity ATT&CK Enterprise Evaluation released in April 2022. The evaluation focused on emulating two of today’s most sophisticated Russian-based threat groups: WIZARD SPIDER and VOODOO BEAR (Sandworm Team).
What XDR Isn't
Why XDR?
Improve Detection, Investigations and Response
Don't Gather Alerts. Hunt Threats.
XDR: A New Vision for InfoSec's Ongoing Problems
Let’s face it. The information security industry loves a new acronym. For industry long-timers, a new acronym might be just the latest reason for an eye roll. For folks new to the field, it can be very confusing. A constructive way to look at XDR — extended detection and response — is as an opportunity to take a fresh look at some old problems and gain clarity.
How Human Intelligence Is Supercharging CrowdStrike's Artificial Intelligence
There is a new trope in the security industry, and it goes something like this: To keep yourself safe, you need an AI-powered solution that can act on its own, and to do that, you need to keep those pesky humans away from it. As a practitioner with a track record of bringing AI to cybersecurity — not because marchitecture demands it these days but because of its actual utility to solve security problems — I find this characterization puzzling.
CrowdStrike and Mandiant Form Mission-Focused Strategic Partnership to Protect Organizations Against Cyber Threats
Falcon Platform Identity Protection Shuts Down MITRE ATT&CK Adversaries
The weeks following the release of the MITRE Engenuity ATT&CK Evaluation can be confusing when trying to interpret the results and cut through the noise. But one thing is crystal clear in this year’s evaluation that every organization should know: The CrowdStrike Falcon® platform stands alone in delivering native identity protection capabilities that shut down adversaries and stop the breach before it even starts.
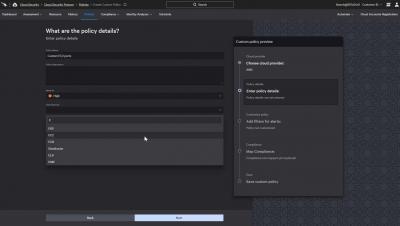
How to Create Custom Cloud Security Posture Policies
How to Create Custom Cloud Security Posture Policies
Falcon Horizon, CrowdStrike’s Cloud Security Posture Management solution, uses configuration and behavioral policies to monitor public cloud deployments, proactively identify issues and resolve potential security problems. However, customers are not limited to predefined policies. This article will review the different options for creating custom cloud security posture management policies in Falcon Horizon.
CrowdStrike "Dominates" in Endpoint Detection and Response
We are excited that Forrester has named CrowdStrike a “Leader” in The Forrester Wave™: Endpoint Detection and Response (EDR) Providers, Q2 2022 and recognized us as dominating in EDR while building our future in extended detection and response (XDR) and Zero Trust. We believe that to be a leader in XDR, you must first be a leader in EDR, which is why we are well-positioned to drive innovation and lead the XDR market forward.
Runtime Protection: The Secret Weapon for Stopping Breaches in the Cloud
Mistakes are easy to make, but in the world of cloud computing, they aren’t always easy to find and remediate without help. Cloud misconfigurations are frequently cited as the most common causes of breaches in the cloud. According to a 2021 survey from VMware and the Cloud Security Alliance, one in six surveyed companies experienced a public cloud security breach or incident due to a cloud misconfiguration in the previous 12 months.
BERT Embeddings: A Modern Machine-learning Approach for Detecting Malware from Command Lines (Part 2 of 2)
CrowdStrike data science researchers recently explored and experimented with the use of Bidirectional Encoder Representation from Transformers (BERT) for embedding command lines, focusing on anomaly detection, but without detailing the model itself. Diving deeper into that research, CrowdStrike researchers explain the reasons for using BERT for command line representation and how to train the model and assess its performance.