Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
July 2020
Getting started with secure DevOps
5 minutes to onboard secure DevOps
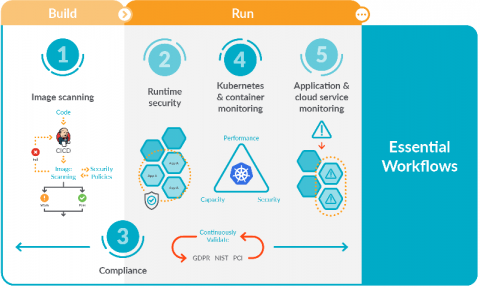
5 Essential workflows for secure DevOps
Focusing on these five essential workflows for secure DevOps will help you get started implementing monitoring, security, and compliance for containers and Kubernetes. You might be starting to adopt DevOps and find that it dramatically simplifies deploying applications in containers and Kubernetes. However, you probably also found that it adds a new set of complexities for managing, securing, and troubleshooting applications.
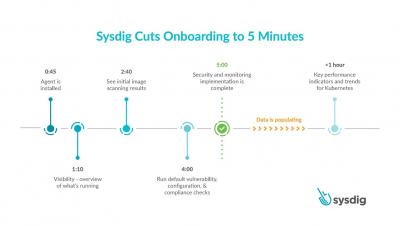
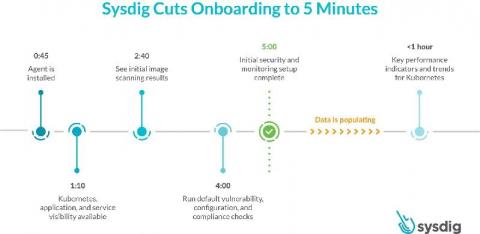
Sysdig cuts onboarding for container and Kubernetes visibility and security to 5 minutes
Today, we are excited to announce a faster onboarding for Kubernetes visibility and security. With the SaaS-first approach and new enhancements to the Sysdig Secure DevOps Platform, you can get results after just a five-minute setup. This release includes a new guided onboarding process, out-of-the-box dashboards as part of curated essential workflows, and a new Sysdig Essentials tier. 5 minutes to onboard secure DevOps - YouTube An error occurred.
12 Container image scanning best practices to adopt in production
Don’t miss out on these 12 image scanning best practices, whether you are starting to run containers and Kubernetes in production, or want to embed more security into your current DevOps workflow. One of the main challenges your teams face is how to manage security risk without slowing down application delivery. A way to address this early is by adopting a Secure DevOps workflow.
Detect CVE-2020-8557 using Falco
A new vulnerability, CVE-2020-8557, has been detected in kubelet. It can be exploited by writing into /etc/hosts to cause a denial of service. The source of the issue is that the /etc/hosts file mounted in a pod by kubelet is not included by the kubelet eviction manager, so it’s not taken into account when calculating ephemeral storage usage by a pod.