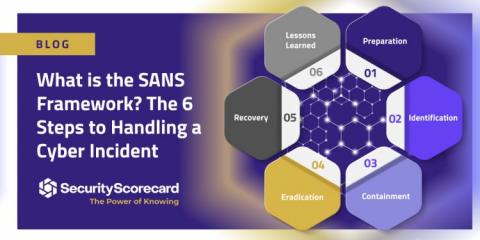
Exploit of Log4Shell Vulnerability Leads to Compromise of Major South American Vaccine Distributor
On June 23, The Cybersecurity and Infrastructure Security Agency (CISA) and the United States Coast Guard Cyber Command (CGCYBER) released a joint Cybersecurity Advisory (CSA) warning network defenders that cyber threat actors, including state-sponsored advanced persistent threat (APT) actors, have continued to exploit CVE-2021-44228 (Log4Shell) in VMware Horizon® and Unified Access Gateway (UAG) servers.