Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
August 2024
The persistent threat: Why major vulnerabilities like Log4Shell and Spring4Shell remain significant
As developers, we're constantly juggling features, fixes, and deadlines. Yet, a lurking issue has been surprisingly overlooked: the continued use of vulnerable Log4j and Spring Framework versions in many projects. Despite the high-profile exposure of Log4Shell and Spring4Shell vulnerabilities, a shocking number of applications are still running on these ticking time bombs. This isn't just a minor oversight — it's a major risk.
Agent hijacking: The true impact of prompt injection attacks
Over the last 18 months, you’ve probably heard about Large Language Models (LLMs) like OpenAI’s GPT and Google’s Gemini. Whether you’re using them as a personal research assistant, an editor, or a data analyst, these tools represent a new frontier of Machine Learning (ML) and Artificial Intelligence (AI) and arguably will have the most significant impact of any technology in this decade.
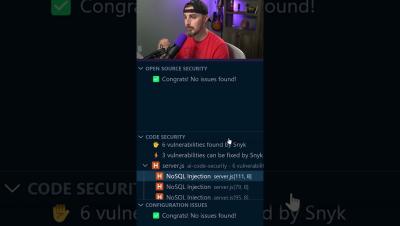
Snyk Code, the only security tool chosen by developers in Stack Overflow's 2024 AI Search and Developer Tools survey
Snyk Code was the only code security tool shortlisted by developers as an AI tool they’ve been regularly using this past year or are looking forward to using next year in Stack Overflow’s recent 2024 AI Search and Developer Tools survey. This underlines Snyk’s dominance as the favorite AI security tool of both developers and security teams and confirms that Snyk Code is providing immense value to developers.
A developer's best friend: Lessons learned from our canine companions about AI code security
Happy International Dog Day! This official holiday celebrates our furry friends and the joy they bring to our lives! Today is particularly special for all of us at Snyk because of our four-legged mascot, Patch the Doberman. But what exactly does a dog have to do with application security? Here at Snyk, we see the idea of a “guard dog” protecting someone’s home as similar to how AppSec solutions can protect today’s development practices.
How AI Almost Got Me FIRED: Part 3
How many jobs has AI lost me now?...Joking! In this video we show you the AI coding tool Cody, and how to use Gemini Pro 1.5 and Mixtral alongside it. We also show how to spot and fix any vulnerabilities that get generated.
Navigating the AI-powered development era in financial services
Australian and New Zealand financial service institutions (FSIs) are facing pressure to innovate quickly while maintaining robust security and regulatory compliance. Many, like ANZ Bank and Commonwealth Bank, are exploring Generative AI to accelerate software development, but is it a silver bullet?
Three trends shaping software supply chain security today
Building software continues to look like an assembly line, with developers pulling resources from across the web to create applications. Although third-party resources have played an essential role in developing software for many years, the way that development teams use these external components looks different today.
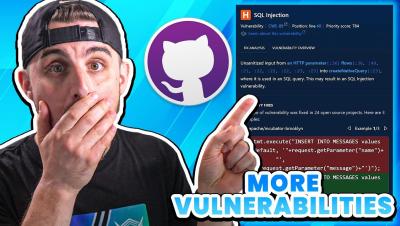
How AI Almost Got Me FIRED: Part 2
This AI Code got me fired again?!...Joking! In this video we show you another AI coding tool called Tabnine and see if it can correctly help you in your coding, as well as how to spot and fix any vulnerabilities it generates.
The journey to AppSec gold: Lessons we can learn from the Olympians
The 2024 Olympics are in full swing, and everyone at Snyk is excited to tune into the games and cheer on our respective countries’ athletes. There’s a lot to love about the Olympics — dazzling opening ceremonies, heart-racing feats, close-call victories, and so much more. But along with all the fun and excitement comes a sense of inspiration.
Vulnerabilities in NodeJS C/C++ add-on extensions
One of the main goals of this research was to explore C/C++ vulnerabilities in the context of NodeJS npm packages. The focus will be on exploring and identifying classic vulnerabilities like Buffer Overflow, Denial of Service (process crash, unchecked types), and Memory Leakages in the context of NodeJS C/C++ addons and modeling relevant sources, sinks, and sanitizers using Snyk Code (see Snyk brings developer-first AppSec approach to C/C++).
InCyber Forum Europe recap: 4 tips from DevSecOps experts
As your organization considers how to shift security left and facilitate shared responsibility for fixing issues, it can be tricky to know where to start. Which tooling will work best with your existing processes? What are the best ways to spread the word about the importance of application security? And once you’ve chosen tools, how do you actually get developers to use them?
Four easy ways to analyze your Java and Kotlin code
Nowadays, the security of your applications is just as important as the functionality they provide. Therefore, analyzing your code for security vulnerabilities is a vital part of maintaining the integrity of your applications and protecting your users' data. As developers, we are at the front lines of this battle. It's our responsibility to ensure that the code we write is not just functional and efficient but also secure.
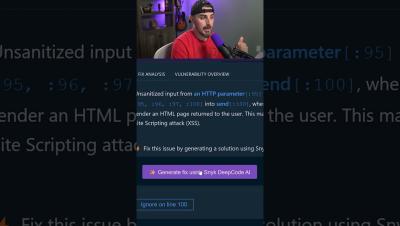
How AI Almost Got Me FIRED: Part 1
This AI code got me fired!!...Not really! But in this video we show you how AI coding tools like Codeium can greatly help accelerate coding , but how they also come with some downfalls and how you can spot them.
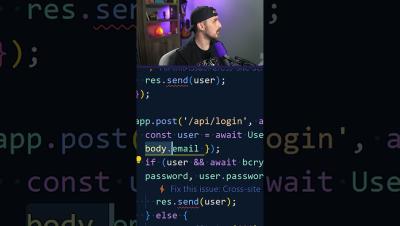
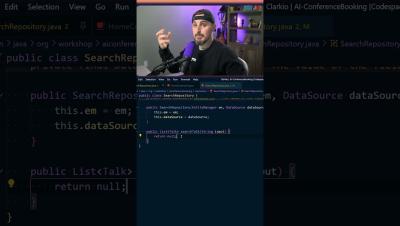
Using GitHub Copilot Chat to Write Secure Code
Watch the full video for more...
A security expert's view on Gartner's generative AI insights - Part 2
Welcome to the second part of our two-part special on Gartner’s “4 Ways Generative AI Will Impact CISOs and Their Teams” report! If you’ve missed the first part on model composition, you can read it here. Today, we will explore why security specialism matters in an AI security tool, particularly where AI quality is concerned.
A security expert's view on Gartner's generative AI insights
Snyk’s goal has always been to empower developers to build fast but safely. This is why we created the developer security category and why we were amongst the first advocates of “shifting left.” Now, AI has changed the equation. According to Gartner, over 80% of enterprises will have used generative AI APIs or models, or deployed their own AI model, by 2026.
Application vulnerability management best practices
Over the years, application vulnerability management has been vital to DevSecOps — which emphasizes shared security responsibility across teams. However, as development practices have evolved, security teams must learn how to adapt and meet developers within their existing workflows. For example, containerization, infrastructure as code (IaC) AI coding assistants, and increased reliance on third-party code are all commonplace in the typical development lifecycle.
Extend the power of your AppSec data with the new Snyk and Snowflake integration
We are thrilled to announce the new Snyk Analytics for Snowflake, allowing Snyk customers to seamlessly access and analyze Snyk’s data from their Snowflake account.
More Ways GitHub Copilot Makes You Vulnerable
Do these suggestions still give us vulnerable code? Or do they make our code less vulnerable? Today we are putting this to the test.
Infosec Europe session: 4 tips for safer AI adoption
AI adoption continues to move at a breakneck speed for businesses across the globe, as shown in a Coatue report comparing AI adoption to early internet adoption and found that AI growth is happening at two times the speed of the former.
Introducing new Snyk AppRisk integrations: Enhancing application risk management with development context
In the fast-paced world of modern software development, grasping the full scope of an application is essential for managing an application security program. This entails having visibility into all the application assets involved in building the app, knowing their ownership, and understanding their importance to the development process and the broader business.