Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
SafeBreach
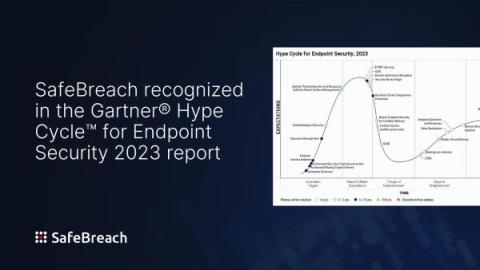
SafeBreach recognized in the Gartner Hype Cycle for Endpoint Security, 2023 report for Second Year in a Row
Now that endpoint detection and response (EDR) solutions have become standard, it’s time to look at what’s next. In light of the ever-increasing attack surface, rampant proliferation of ransomware, and continued remote work environments, security leaders must proactively find new and innovative tools to protect endpoints from attack.
Navigating the Path to Continuous PCI Compliance and Security Validation with Breach and Attack Simulation
The first deadline for compliance with the Payment Card Industry Data Security Standard (PCI DSS) Version 4.0 is March 31, 2024. If your v4.0 compliance initiative is not already underway, it should be a major priority over the next 2–3 quarters.
AMOS Infostealer, BiBi Wiper, FreeWorld Ransomware, and More: Hacker's Playbook Threat Coverage Round-up: November 2023
In this version of the Hacker’s Playbook Threat Coverage round-up, we are highlighting newly added coverage for several recently discovered or analyzed ransomware and malware variants, including NoEscape ransomware, AvosLocker ransomware, and Retch ransomware, amongst others. SafeBreach customers can select and run these attacks and more from the SafeBreach Hacker’s Playbook™ to ensure coverage against these advanced threats.
Citrix Bleed Vulnerability: SafeBreach Coverage for US-CERT Alert (AA23-325A)
On November 21st, the Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), Multi-State Information Sharing & Analysis Center (MS-ISAC), and Australian Signals Directorate’s Australian Cyber Security Center (ASD’s ACSC) released an advisory highlighting the ongoing exploit of the Citrix Bleed Vulnerability (CVE-2023-4966) by Lockbit 3.0 affiliates.
Complying with Confidence: Navigating Cybersecurity Regulation and Legislation
From compliance with more rigorous cybersecurity regulations to navigating the shifting complexities of cyber liability insurance, CISOs and other cybersecurity leaders are gaining a growing number of non-technical responsibilities.
Weather Forecast: Money Is Going to Rain from the Cloud
Since the start of Bitcoin in 2009, the popularity and prevalence of cryptocurrencies has exploded, resulting in a net worth of over $1 trillion that continues to grow. Cryptocurrency—held in virtual wallets—is obtained by users who purchase coins on a cryptocurrency exchange, receive coins as payment from someone else, or “mine” coins virtually themselves.
Are we safer today than we were yesterday?
In the first two installments of this three-part series based on our recent white paper, The Skeptic’s Guide to Buying Security Tools, we provided an evidence-based approach to helping your organization justify a new security tool purchase and key considerations to future-proof that investment. In today’s post, we’ll discuss how to evaluate the efficacy of that tool once you’ve made the purchase and implemented it within your security ecosystem.