Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vanta
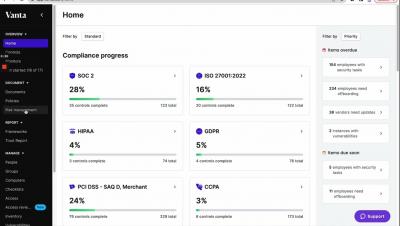
What is continuous security monitoring?
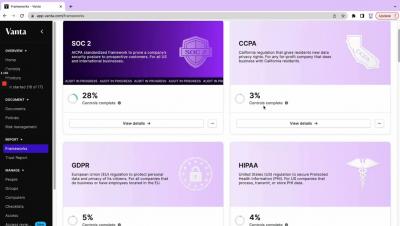
Continuous security monitoring refers to an ongoing monitoring system that keeps a constant watch for security vulnerabilities, the state of your information security controls, and potential risks and threats to your information security. If you think too much about information security, it can seem insurmountable. At any given moment, there could be teams of hackers trying everything in their power to get access to your data.
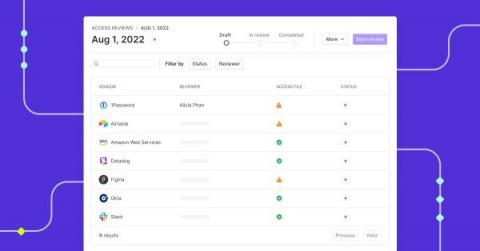
How do you perform quarterly access reviews?
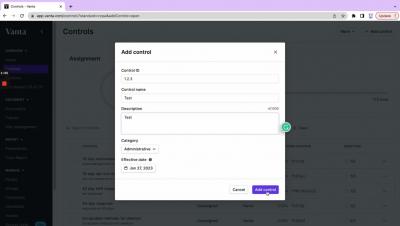
Savvy organizations usually deploy some type of identity and access management (IAM) solution. IAM solutions leverage the principle of least privilege (POLP), role-based access control (RBAC), or other such mechanisms to manage access to data, applications, and IT infrastructure. However, every organization's structure and human resources capacity typically change over time as new employees are brought on board and existing ones quit.
Reimagining the future of trust with Trustpage by Vanta
Vanta’s mission is to secure the internet and protect consumer data. An important step to making this a reality is ensuring that every company can prove its own security to customers and prospects—creating a virtuous cycle where good security is good business. Today, we're thrilled to announce the next move in achieving our mission with Vanta's acquisition of Trustpage to reimagine the future of trust together.
What is vulnerability scanning?
Vulnerability scanning is the action of conducting an automated review of your system to look for potential risks and vulnerabilities. For budding information security professionals (or even those who have worked in the field for years), there is always something new to learn. Not only is it a highly intricate and advanced field but, on a daily basis, there is a cat-and-mouse game happening between security engineers and hackers.