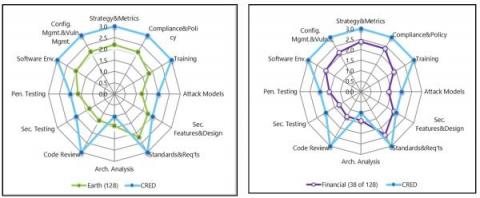
Cybersecurity Research Center Developer Series: The OWASP Top 10
In this new Cybersecurity Research Center series, we analyze the OWASP Top 10, which is a list of the most common vulnerabilities in web applications. In application security, the Open Web Application Security Project (OWASP) Top 10 list is a valuable resource for DevSecOps teams that oversee the development and security of web applications. The OWASP Top 10, updated every four years, lists the most common vulnerabilities in web apps based on a consensus among contributors from the OWASP community.