Integrating MITRE ATT&CK with Cloud SOAR to optimize SecOps and Incident Response
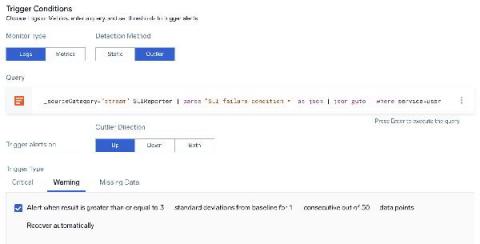
Today’s complex cyber threats leave no room for mediocrity. Security analysts must know who is attacking them, how the attacker gained access, what methods they used to infiltrate your systems, and what their next move might be. However, modern cyber threats leave no recognizable patterns in their behavior, making threat anticipation harder than ever. To boost their threat hunting capabilities, SOC teams must implement advanced technologies and strategic techniques.