Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Sysdig
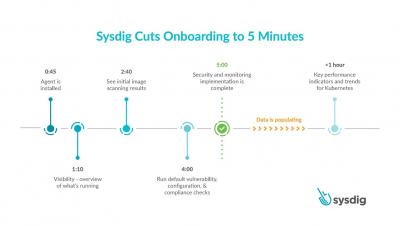
12 Container image scanning best practices to adopt in production
Don’t miss out on these 12 image scanning best practices, whether you are starting to run containers and Kubernetes in production, or want to embed more security into your current DevOps workflow. One of the main challenges your teams face is how to manage security risk without slowing down application delivery. A way to address this early is by adopting a Secure DevOps workflow.
Detect CVE-2020-8557 using Falco
A new vulnerability, CVE-2020-8557, has been detected in kubelet. It can be exploited by writing into /etc/hosts to cause a denial of service. The source of the issue is that the /etc/hosts file mounted in a pod by kubelet is not included by the kubelet eviction manager, so it’s not taken into account when calculating ephemeral storage usage by a pod.
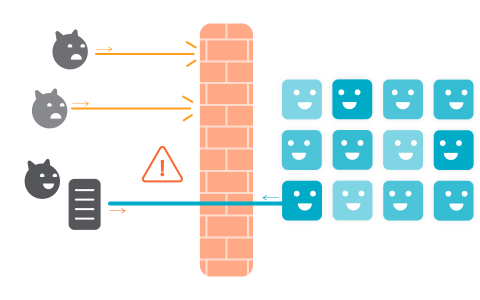
File Integrity Monitoring: Detecting suspicious file activity inside a container
In this blog, we will explore suspicious file activity inside a container and see how to effectively implement a file integrity monitoring (FIM) workflow. We’ll also cover how Sysdig Secure can help you implement FIM for both containers and Linux hosts.
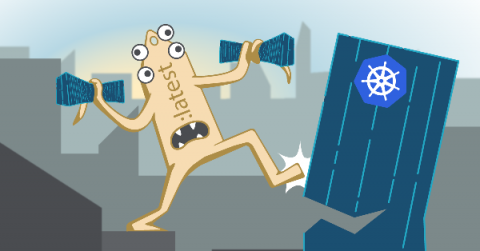
Attack of the mutant tags!Or why tag mutability is a real security threat
Tag mutability can introduce multiple functional and security issues. In container land, tags are a volatile reference to a concrete image version in a specific point in time. Tags can change unexpectedly, and at any moment. In this article, we’ll learn how we can prevent them.
Azure you shot an ARO through our hearts... Confidently observe and secure Azure Red Hat OpenShift with Sysdig and Arctiq
It has arrived! Azure Red Hat OpenShift 4 is here and generally available; now, how do you add even more granular security and faster time to repair (MTTR) for your teams? Sysdig, that’s how!
Extending security and governance with Sysdig and IBM Cloud Pak for Multicloud Management
Detect CVE-2020-8555 using Falco
This CVE is a Server Side Request Forgery (SSRF) vulnerability in kube-controller-manager that allows certain authorized users to leak up to 500 bytes of arbitrary information from unprotected endpoints within the master’s host network (such as link-local or loopback services).
Detect reverse shell with Falco and Sysdig Secure
Reverse shell is a way that attackers gain access to a victim’s system. In this article, you’ll learn how this attack works and how you can detect it using Falco, a CNCF project, as well as Sysdig Secure. Sometimes, an application vulnerability can be exploited in a way that allows an attacker to establish a reverse shell connection, which grants them interactive access to the system.
Expanding the IBM & Sysdig Relationship to Manage Cloud Security Risk
Today, we are pleased to announce the expansion of Sysdig’s relationship with IBM to extend cloud security governance with IBM Cloud Pak for Multicloud Management. Through a new OEM agreement, Sysdig Secure and the Sysdig Secure DevOps Platform are now available through IBM and IBM Business Partners. The combined IBM and Sysdig offering delivers centralized cloud visibility, governance and automation with in-depth container security intelligence for Red Hat OpenShift.