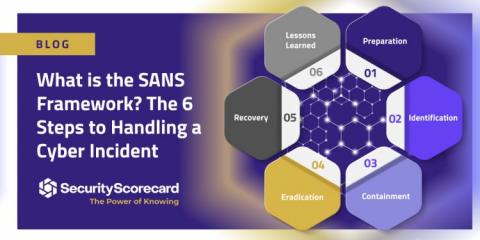
What is the SANS Framework? The 6 Steps to Handling a Cyber Incident
A cyber incident can range from a minor power outage to a full-scale cyber attack. No matter the incident scale, having clear guidelines to follow can help organizations create effective and standardized response plans. The SysAdmin, Audit, Network, and Security (SANS) Institute is one of the leading organizations providing cybersecurity training, research, and certification.