Introducing Vanta Trust Center and the State of Trust Report
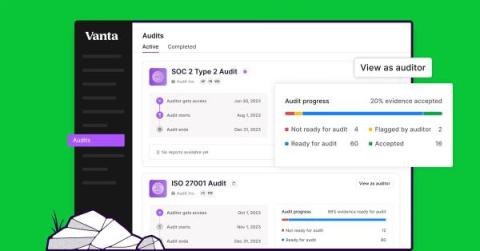
Today we’re thrilled to introduce Vanta Trust Center, a centralized source of truth for companies to showcase their security posture confidently. Following Vanta’s acquisition of Trustpage earlier this year, Trust Center combines the capabilities of Trustpage Trust Centers and Vanta Trust Reports, making it easier than ever for customers to automatically manage their workflows and accelerate the security review process — all from within Vanta.