How Mergers & Acquisitions Are Leaving Your APIs Vulnerable #apiattacks #apimanagement #api
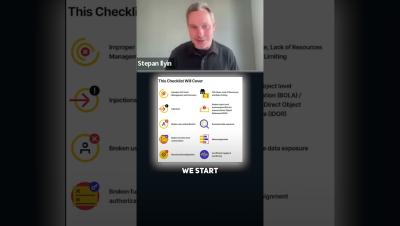
Mergers and acquisitions can expose critical API vulnerabilities, often overlooked due to poor documentation and lack of standardization. Learn about the hidden risks that can lead to delayed incident response and compromised security during M&A processes.