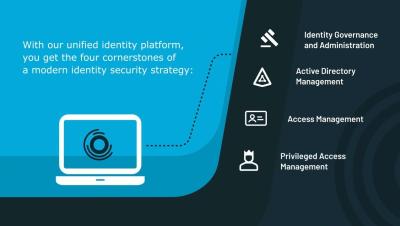
Identity risk management: What is it and how can you achieve it?
Risk. It’s more than just an infuriating board game from your childhood. And when identity risk is involved in your cybersecurity landscape – and it will be involved, since identity is one of the most easily accessible and most frequently attacked facets of your IT environment – the potential consequences of its compromise extend well beyond losing control of a fantasy continent on a game board.