What Cybersecurity Risks Does Typosquatting Pose, and How Can You Beat Them?
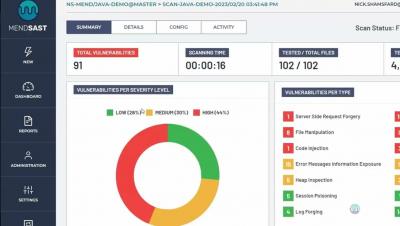
Typosquatting represents a significant threat to cybersecurity. But what exactly is it? How does it work? What threats does it pose to your cybersecurity? How can you prevent these threats and how can you deploy application security against them?