Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
October 2022
Advisory: New OpenSSL Critical Security Vulnerability
Last week, the OpenSSL Project announced that on Tuesday, November 1, 2022 1300-1700 (UTC), they will release OpenSSL version 3.0.7 to address a critical CVE.
It's Cybersecurity Awareness Month-So Let's Talk Automation and Home Security
At this point, anybody in the IT world would have to be living in a cave in the wilderness to not know that October is Cybersecurity Awareness Month. (And since there’s no Wi-Fi in wilderness caves, that scenario is admittedly unlikely.) This week, I wanted to take a closer look at a couple topics, one for work and one at home.
Async Inventory Reporting for Organizations & Accounts
WebStorm Integration
Modern AppSec Moves Beyond Shift Left to Shift Smart
This is the third of a six-part blog series that highlights findings from a new Mend white paper, Five Principles of Modern Application Security Programs. Be sure to look out for our upcoming blogs on each of the five principles.
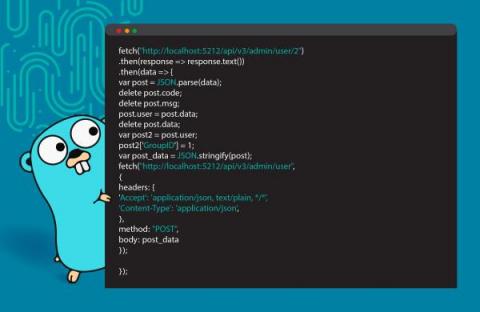
A Rash of Recent CVEs in Go
At 12 years old, Go is a relatively new programming language–but it’s a popular one when it comes to cloud-native computing. CockroachDB, Docker, Kubernetes, and AdGuardHome (byAdGuard) are all built on Go, and the Go GitHub repository has over 105,000 stars, putting it in third place as a GitHub star leader.
Meticulous Prep and Planning-A Linchpin of Modern AppSec Programs
This is the second of a six-part blog series that highlights findings from a new Mend white paper, Five Principles of Modern Application Security Programs. Be sure to look out for our upcoming blogs on each of the five principles. It’s no exaggeration to say that IT and application security teams from all organizations are facing a perfect storm.
Vulnerability Research: Here's How it Works at Mend
There are many types of security research, from digging into malware to discovering the latest DDoS attack vectors. At Mend, vulnerability research is a primary focus for our research team, but even that area has many different avenues to pursue. For example, we tend to focus on open source vulnerabilities, so it is quite unlikely that you’ll see us doing reverse engineering and trying to understand assembly code.
To use rest_client, or to use rest-client, that is the question
Rest-client is one of the most popular RubyGems, with a simple DSL that allows sending HTTP requests. Lightweight, versatile, developed by famous Rubyists…with all these attributes, this gem is a very shiny and attractive target for malicious actors. All they need is a good method of attack. An attempt made today tried to leverage typosquatting by adding malicious code to rest_client, but it didn’t quite ace the assignment.
It's Cybersecurity Awareness Month-Let's Talk AppSec
It’s that time of year again: October is Cybersecurity Awareness Month. At the very least, it serves as an annual reminder to check your security posture, both at work and at home. But I figured that it also might be a good time to take a closer look at more specific topics over the course of the month. I will do my best to stay out of the weeds, but this is important for all of us to be aware of.
Must-Know Facts About Evil-Colon Attacks
In a new article for HelpNet Security, Leon Juranic, security research team lead at Mend, states the case for taking proactive defensive steps against a new attack called Evil-Colon. Evil-Colon works similarly to the now defunct Poison-NULL-Byte attacks, and it has the potential to cause severe disruption to your code if not properly addressed. What does all this mean? In a nutshell, it’s possible to exploit applications that are performing path-based operations with user input in various ways.
Why Building a Modern AppSec Program is Vital for Digital Business
This is the first of a six-part blog series that highlights findings from a new Mend white paper, Five Principles of Modern Application Security Programs. Be sure to look out for our upcoming blogs on each of the five principles. The COVID-19 pandemic accelerated the digitalization plans for global organizations by three years, while the adoption rate for digitized products and services increased by seven years.
Six Golden Rules for Software and Application Security
October is Cybersecurity Awareness Month, established back in 2004 by the Office of the U.S. President and the U.S. congress. Led by the Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA), the initiative helps both individuals and enterprises make smarter, more informed security decisions.
Are You CODEfident?
We’ve been watching the global transition to an app-driven world for some time now, as companies develop and deploy innovative software at warp speed. And we’ve also watched application security teams struggle to keep up. Many try to use yesterday’s tools for today’s AppSec reality, while others wrestle with immature application security programs. And that’s when we realized: modern application security programs are different. They run on CODEfidence. Let me explain.
Cybercriminals targeted users of packages with a total of 1.5 billion weekly downloads on npm
Another week, another supply chain incident. It’s been only nine days since the Mend research team detected the dYdX incident, and today we have detected another supply chain malicious campaign. On October 02, 2022 at 12:12 UTC, a new npm account was registered, and a package called nuiversalify was immediately uploaded. The same threat actor then proceeded to publish more typo/spellcheck squattings of popular packages until 14:03:29 UTC, with small but irregular time gaps between uploads.